

What is a DDoS attack?
A DDoS attack (Distributed Denial of Service Attack) is a hacker attack that aims to stop or partially delay the services of a given resource (called a victim), making them inaccessible to its target users.
The most common victims are well-known web servers, with the aim being to overload the targeted server or virtual resource, so that it is unable to execute requests from the internet.
How can that affect your business?
Loss of customers
Reputation Disruption
Financial losses
How does our system work?

Types of DDoS attacks
TCP:
- Invalid TCP MSS
- Invalid TCP WIN
- Invalid TCP SEQ
- TCP Statefull check
- Fragmented ACK Attack
- Booters TCP Flood
- TCP SYN+ACK Flood
- TCP FIN Flood
- TCP RESET Flood
- TCP ACK + PSH Flood
- TCP Fragments
- HTTP Flood
- HTTPS Flood
- Brute Force
- Connection Flood
- Low rate attack
- Slowloris Flood
- Apache Killer
- Buffer Overflow Attack
- LOIC (Low Orbit Ion Cannon)
UDP:
- Booters UDP scripts
- Invalid Checksum
- Invalid TTL
- Invalid Packet size
- HPING3 flooder
- UDP null packets
- DNS Reflection
- NTP Reflection
- SSDP Reflection
- MSSQL Reflection
- Portmap Reflection
- Chargen Reflection
- SNMP Reflection
- Bittorrent Reflection
- Memcached Reflection
- TFTP Reflection
- RIP Reflection
- LDAP Reflection
Other:
- IP Spoofed packets
- ICMP port unreachable
- ICMP flood
- Smurf Attack
- Ping of Death
- Teardrop Attack
- SIP Attacks
- IPSec Attacks
With each new type of DDoS attack on our client's IP address, different from the ones known so far, we apply filtering to stop malicious traffic. The detected threat is then registered automatically for all existing clients. This protects the entire network and infrastructure from every new type of DDoS attack as soon as it is detected for the first time.

The Solution
S3 Company has its own DDoS protection system.
Like most successful products, this one was born out of the need for a better solution than the ones currently available.
Our experience dates back to 2014, when our servers began receiving daily DDoS attacks. We did tests with several existing firewall systems, but they all had many drawbacks (mostly with failing to stop attacks).
The solution was to create our own system for DDoS protection, because the most important thing when countering a new type of attack is the response time and the ability to make changes quickly. Our system analyzes traffic in real time and allows you to quickly add new rules and filters.

Why does our DDoS protection solution work?
With each new type of DDoS attack on our client's business, which differs from the ones known so far, we apply filtering to stop malicious traffic.
The new threat is then registered automatically for all existing clients.
Thus, the entire network and infrastructure is protected from all new types of DDoS attacks as soon as they are detected for the first time.
Thanks to the various types of businesses that trust us and our update policy, our solution against DDoS attacks is well refined, repeatedly tested, improved and always in line with new attacks.

Advantages of our protection
-
1Easy activation - no need to reconfigure your existing communication equipment
-
2Consultation and full support before and after the activation of DDoS protection
-
3Your traffic will never be blackhole!
-
4Limitless scalability through cluster technology
-
5Possibility for devices to work on Layer 2 (bridge) and Layer 3 (routing)
-
6Possibility for 10G / 40G / 100G / 400G ports
-
7Redundancy - High Master-Master type Availability with full replication between devices
-
8Interactive Web panel for clients, with the ability to change the protection configuration

Technical parameters
- Linux based systems with custom network stack
- Hardware-accelerated network adapters for raw filtering
- Option for bidirectional and unidirectional traffic analyze and filtering
- Fully compatible with RFC design and parameters
- Stops attacks up to 1000 Gbps

Our DDoS protection solution can be provided in several ways
Internet connectivity provided by S3 - the client receives pure traffic, because in the presence of an attack, it is automatically filtered and the client does not even know about it.
There are two possibilities:
- Static - by providing our IP addresses
- Dynamically - by means of BGP

Тechnical configuration method
- Colocation of a server in S3 (renting a physical or virtual one) - an internet connection is built in S3 Data Center or in one of the partner data centers, via cross-connect
- Installation of physical equipment at the customer premises - suitable for telecoms and corporate customers who have sufficient Internet capacity to install equipment at them to filter attacks in their network.
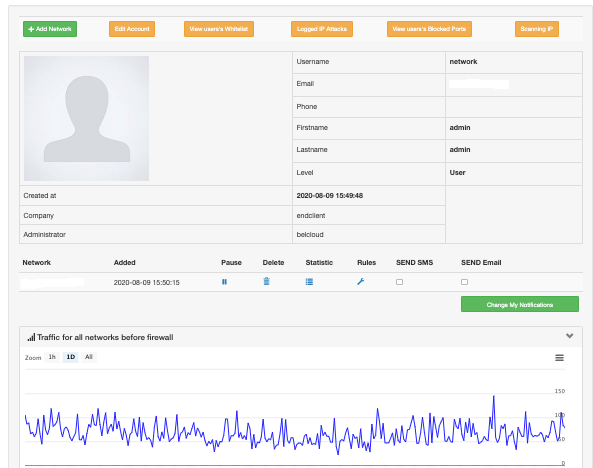
More about the user portal
Developed by S3, this self-managed portal allows you to monitor a cluster of devices that protect the customer.
Advantages of the portal:
- easy access via username and password
- allows monitoring of traffic graphs (clean and malicious)
- a list of detailed information for each attack
- notification by e-mail and sms at an event
- management of DDоS protection itself - stopping, running rules, activating static adsale filters, black & white list of IP addresses and networks.

Our clients
Our clients are hundreds from all areas of business:
- Banks and financial institutions
- Government organizations
- E-shops
- Media
- Gaming servers and much more.






.svg)
.svg)


